Jun 27, 2010
KORELASI
HIPOTESA
Pengertian : Pendapat sementara yang masih perlu diuji kebenarannya.
Rumusan Hipotesa:
Ho: Hipotesis null atau hipotesa nihil/kerja. Rumusan dengan menggunakan asas praduga bersalah.
H1= Ha : Hipotesis alternatif atau tandingan
Rumusan ini berlaku apabila Ho tidak berlaku atau ditolak.
Kesimpulan Hipotesa
Jika sig >α maka Ho diterima, Ha ditolak
Berarti tidak ada hubungan antar 2 variabel
Jika sig <α maka Ho ditolak, Ha diterima
Berarti ada hubungan antar 2 variabel
Keterangan:
Sig: signifikan/ keterikatan/ hubungan antar 2 var
α: alpha besarnya bisa 0,01 atau 0,05
uji korelasi
Uji Korelasi akan mencari besarnya hubungan dan arah hubungan antar 2 variabel.
Analisis Korelasi
1. Berdasarkan Arahnya
*Apabila positif (+) maka hubungannya searah
( jika 1 variabel naik maka yang lain ikut naik)
*Apabila negatif (-) maka hubungannya berlawanan
( jika 1 variabel naik maka yang lain turun)
2. Hubungan antar 2 variabel
Berdasarkan nilai derajat korelasinya baik positf maupun negatif
0,7 s/d 1 kuat
0,4 s/d 0,7 sedang
0,2 s/d 0,4 rendah
< 0,2 lemah/ diabaikan/ dianggab tidak ada hubungan antar 2 variabel 3. Berdasarkan Hipotesanya
Dengan Uji Signifikan
Jika sig > α maka Ho diterima, Ha ditolak
Berarti tidak ada hubungan antar 2 variabel
Jika sig < α maka Ho ditolak ,Ha diterima Berarti ada hubungan antar 2 variabel Keterangan: Sig: signifikan/ keterikatan/ hubungan antar 2 var α: alpha besarnya bisa 0,01 atau 0,05 Jika tandanya * berarti 0,05 (5%)->kurang akurat
Jika tandanya ** berarti 0,01 (1%)->akurat
4. Berdasarkan Uji t Hitung dibanding t Tabel
Jika t Hitung > t Tabel, maka Ha diterima
Berarti ada hubungan antar 2 variabel
Jika t Hitung < t Tabel, maka Ha ditolak
Berarti tidak ada hubungan antar 2 variabel
Jadi kebalikan dari uji signifikan Read more "KORELASI..."
Pengertian : Pendapat sementara yang masih perlu diuji kebenarannya.
Rumusan Hipotesa:
Ho: Hipotesis null atau hipotesa nihil/kerja. Rumusan dengan menggunakan asas praduga bersalah.
H1= Ha : Hipotesis alternatif atau tandingan
Rumusan ini berlaku apabila Ho tidak berlaku atau ditolak.
Kesimpulan Hipotesa
Jika sig >α maka Ho diterima, Ha ditolak
Berarti tidak ada hubungan antar 2 variabel
Jika sig <α maka Ho ditolak, Ha diterima
Berarti ada hubungan antar 2 variabel
Keterangan:
Sig: signifikan/ keterikatan/ hubungan antar 2 var
α: alpha besarnya bisa 0,01 atau 0,05
uji korelasi
Uji Korelasi akan mencari besarnya hubungan dan arah hubungan antar 2 variabel.
Analisis Korelasi
1. Berdasarkan Arahnya
*Apabila positif (+) maka hubungannya searah
( jika 1 variabel naik maka yang lain ikut naik)
*Apabila negatif (-) maka hubungannya berlawanan
( jika 1 variabel naik maka yang lain turun)
2. Hubungan antar 2 variabel
Berdasarkan nilai derajat korelasinya baik positf maupun negatif
0,7 s/d 1 kuat
0,4 s/d 0,7 sedang
0,2 s/d 0,4 rendah
< 0,2 lemah/ diabaikan/ dianggab tidak ada hubungan antar 2 variabel 3. Berdasarkan Hipotesanya
Dengan Uji Signifikan
Jika sig > α maka Ho diterima, Ha ditolak
Berarti tidak ada hubungan antar 2 variabel
Jika sig < α maka Ho ditolak ,Ha diterima Berarti ada hubungan antar 2 variabel Keterangan: Sig: signifikan/ keterikatan/ hubungan antar 2 var α: alpha besarnya bisa 0,01 atau 0,05 Jika tandanya * berarti 0,05 (5%)->kurang akurat
Jika tandanya ** berarti 0,01 (1%)->akurat
4. Berdasarkan Uji t Hitung dibanding t Tabel
Jika t Hitung > t Tabel, maka Ha diterima
Berarti ada hubungan antar 2 variabel
Jika t Hitung < t Tabel, maka Ha ditolak
Berarti tidak ada hubungan antar 2 variabel
Jadi kebalikan dari uji signifikan Read more "KORELASI..."
Labels:
Statistik
Arsitektur LCDUI
Berikut hierarki dari class-class yang diambil dari paket lcdui
( javax.microedition.lcdui) Dari class-class user interface dapat langsung ditampilkan ke layar hanya turunan dari class Displayable.
MIDAlert.java
import javax.microedition.lcdui.*;
import javax.microedition.midlet.*;
public class MIDAlert extends MIDlet implements CommandListener {
private Display display;
private Form form;
private Alert alert;
private Command cmdExit;
private Command cmdAlert;
public MIDAlert() {
display = Display.getDisplay(this);
//membuat objek Form
form = new Form("Demo Alert");
//membuat objek Command
cmdExit = new Command("Exit", Command.EXIT, 1);
cmdAlert = new Command("Alert", Command.SCREEN, 2);
//menambahkan objek Command "cmdExit" dan "cmdAlert"
form.addCommand(cmdExit);
form.addCommand(cmdAlert);
//menset event
form.setCommandListener(this);
} public void startApp() {
//menentukan objek yang ditampilkan di layar
display.setCurrent(form);
} public void pauseApp() {
}
public void destroyApp(boolean unconditional) {
}
public void commandAction(Command c, Displayable d) {
if (c == cmdAlert) {
//memanggil method tampilAlert
tampilAlert();
} else if (c == cmdExit) {
destroyApp(true);
notifyDestroyed();
}
}
private void tampilAlert() {
try {
//membuat objek Alert dan menentukan String yang ditampilkan
alert = new Alert("Informasi", "Pesan ini tampil di User", null, null);
//menentukan tipe Alert
alert.setType(AlertType.ALARM);
//menentukan lamanya Alert tampil
alert.setTimeout(5000);
//menampilkan Alert
display.setCurrent(alert);
} catch(Exception e) {
System.out.println(e.getMessage());
}
}
}
Sebuah aplikasi biasanya ketika menampilkan pesan menggunakan icon atau gambar tertentu, berikut tambahan kode program agar pesan yang ditampilkan di atas dapat menampilkan pesan yang disertai dengan gambar.Hasil output dari program di atas adalah
Read more "Arsitektur LCDUI..."
( javax.microedition.lcdui) Dari class-class user interface dapat langsung ditampilkan ke layar hanya turunan dari class Displayable.
MIDAlert.java
import javax.microedition.lcdui.*;
import javax.microedition.midlet.*;
public class MIDAlert extends MIDlet implements CommandListener {
private Display display;
private Form form;
private Alert alert;
private Command cmdExit;
private Command cmdAlert;
public MIDAlert() {
display = Display.getDisplay(this);
//membuat objek Form
form = new Form("Demo Alert");
//membuat objek Command
cmdExit = new Command("Exit", Command.EXIT, 1);
cmdAlert = new Command("Alert", Command.SCREEN, 2);
//menambahkan objek Command "cmdExit" dan "cmdAlert"
form.addCommand(cmdExit);
form.addCommand(cmdAlert);
//menset event
form.setCommandListener(this);
} public void startApp() {
//menentukan objek yang ditampilkan di layar
display.setCurrent(form);
} public void pauseApp() {
}
public void destroyApp(boolean unconditional) {
}
public void commandAction(Command c, Displayable d) {
if (c == cmdAlert) {
//memanggil method tampilAlert
tampilAlert();
} else if (c == cmdExit) {
destroyApp(true);
notifyDestroyed();
}
}
private void tampilAlert() {
try {
//membuat objek Alert dan menentukan String yang ditampilkan
alert = new Alert("Informasi", "Pesan ini tampil di User", null, null);
//menentukan tipe Alert
alert.setType(AlertType.ALARM);
//menentukan lamanya Alert tampil
alert.setTimeout(5000);
//menampilkan Alert
display.setCurrent(alert);
} catch(Exception e) {
System.out.println(e.getMessage());
}
}
}
Sebuah aplikasi biasanya ketika menampilkan pesan menggunakan icon atau gambar tertentu, berikut tambahan kode program agar pesan yang ditampilkan di atas dapat menampilkan pesan yang disertai dengan gambar.Hasil output dari program di atas adalah
Read more "Arsitektur LCDUI..."
Labels:
java
user interface
Pembuatan user interface
Satu hal terpenting dalam sebuah aplikasi adalah Graphical User Interface (GUI). GUI dapat dimanfaatkan sebagai media input dalam sebuah aplikasi. Class-class untuk membangun GUI dalam MIDP disimpan dalam lcdui (javax.microedition.lcdui), agar dapat memanfaatkan class tersebut harus dilakukan dengan mengimport paketnya.
Struktur GUI dalam MIDP
GUI di dalam MIDP dibagi menjadi dua bagian, yaitu:
high-level API (yang didasarkan pada penbentukan window) dan
low-level API (yang didasarkan pada pembentukan canvas dan pixel).
Penggunaan high-level API lebih mudah dibanding mengunakan low-level API untuk membangun sebuah interface pada suatu aplikasi. Namun dengan menggunakan low level API,kita dapat lebih leluasa dalam mendesain sebuah interface.
Model high-level API menyediakan class-class standar yang digunakan untuk membangun UI (User Interface) seperti component Form, TextBox, List, Alert. Model High-level mengimplementasikan class-class yang diturunkan dari class Screen. Model Low-level API memberikan akses yang kepada programmer untuk melakukan control terhadap tampilan layer, termasuk pengembaran menggunakan pixel,pembentukan bentuk geometri (segitiga, segiempat,lingkaran,elips, arc, dll). Model ini sering digunakan untuk membuat game. Karena model ini dapat membuat bentuk tek graphic yang lebih spesifik sesaui dengan keinginan. Model ini juga dapat membaca tombol-tombol yang ditekan oleh user. Dalam paket lcdui yang dimport menggunakan: import javax.microedition.lcdui.*; Paket ini terdiri dari interface dan class.
Tabel daftar interface:
Interface Keterangan
Choice Mengimplementasikan sejumah item pilihan yang didefinisikan. CommandListener Menerima event-event level tinggi. Menerima event yang mengindikasikan perubahan keadaan Item State Listener dari item yang terdapat pada obyek Form Daftar kelas paket lcdui.
Class Keterangan
Alert Menampilkan pesan ke user untuk periode waktu tertentu .
AlertType Mendefinisikan tipe objek Alert yang akan ditampilkan.
Canvas adalah Class yang digunakan untuk aplikasi yang membutuhkan event. event rendah seperti game dan untuk mengambar dilayar.
ChoiceGroup Meyajikan sekumpulan elemen yang dapat dipilih yang dimasukkan di dalam Form.
Command Konstruksi yang mebungkus informasi-informasi yang dilakukan oleh user.
CustomItem Membuat elemen user interface baru yang ditempatkan pada sebuah Form.
DateField Komponen yang digunakan untuk menampilkan tanggal danwaktu. Display Manager tampilan
Displayable Objek yang memiliki kemampuan ditampilkan pada layar.
Font Mengatur huruf yang akan ditampilkan ke layar. Gauge Tampilan grafis yang digunakan untuk memvisualisasikan nilai tertentu yang diletakkan pada Form.
Graphics Menyediakan kemampuan menggambar pada sebuah Canvas.
Image Digunakan untuk menyimpan data gambar.
ImageItem Meyediakan kotrol layout untuk gambar-gambar yang ditempatkan pada sebuah Form.
Item Kelas dasar untuk menempatkan komponen-komponen yangdapat ditempatkan pada sebuah Form.
List Layar yang berisi daftar pilihan. Screen Kelas dasar semua komponen layar dalam high-level user interface.
StringItem Item yang berisi string yang kemudian ditempatkan pada Form.
TextBox Layar yang mengijinkan user memanipulasi teks dan bisa juga dijadikan media input.
TextField Komponen untuk memasukkan teks di atas Form. Ticker Bagian teks yang berjalan terus-menerus di atas layar.
Ticker tidak dapat ditempelkan pada Canvas.
. Read more "user interface..."
Satu hal terpenting dalam sebuah aplikasi adalah Graphical User Interface (GUI). GUI dapat dimanfaatkan sebagai media input dalam sebuah aplikasi. Class-class untuk membangun GUI dalam MIDP disimpan dalam lcdui (javax.microedition.lcdui), agar dapat memanfaatkan class tersebut harus dilakukan dengan mengimport paketnya.
Struktur GUI dalam MIDP
GUI di dalam MIDP dibagi menjadi dua bagian, yaitu:
high-level API (yang didasarkan pada penbentukan window) dan
low-level API (yang didasarkan pada pembentukan canvas dan pixel).
Penggunaan high-level API lebih mudah dibanding mengunakan low-level API untuk membangun sebuah interface pada suatu aplikasi. Namun dengan menggunakan low level API,kita dapat lebih leluasa dalam mendesain sebuah interface.
Model high-level API menyediakan class-class standar yang digunakan untuk membangun UI (User Interface) seperti component Form, TextBox, List, Alert. Model High-level mengimplementasikan class-class yang diturunkan dari class Screen. Model Low-level API memberikan akses yang kepada programmer untuk melakukan control terhadap tampilan layer, termasuk pengembaran menggunakan pixel,pembentukan bentuk geometri (segitiga, segiempat,lingkaran,elips, arc, dll). Model ini sering digunakan untuk membuat game. Karena model ini dapat membuat bentuk tek graphic yang lebih spesifik sesaui dengan keinginan. Model ini juga dapat membaca tombol-tombol yang ditekan oleh user. Dalam paket lcdui yang dimport menggunakan: import javax.microedition.lcdui.*; Paket ini terdiri dari interface dan class.
Tabel daftar interface:
Interface Keterangan
Choice Mengimplementasikan sejumah item pilihan yang didefinisikan. CommandListener Menerima event-event level tinggi. Menerima event yang mengindikasikan perubahan keadaan Item State Listener dari item yang terdapat pada obyek Form Daftar kelas paket lcdui.
Class Keterangan
Alert Menampilkan pesan ke user untuk periode waktu tertentu .
AlertType Mendefinisikan tipe objek Alert yang akan ditampilkan.
Canvas adalah Class yang digunakan untuk aplikasi yang membutuhkan event. event rendah seperti game dan untuk mengambar dilayar.
ChoiceGroup Meyajikan sekumpulan elemen yang dapat dipilih yang dimasukkan di dalam Form.
Command Konstruksi yang mebungkus informasi-informasi yang dilakukan oleh user.
CustomItem Membuat elemen user interface baru yang ditempatkan pada sebuah Form.
DateField Komponen yang digunakan untuk menampilkan tanggal danwaktu. Display Manager tampilan
Displayable Objek yang memiliki kemampuan ditampilkan pada layar.
Font Mengatur huruf yang akan ditampilkan ke layar. Gauge Tampilan grafis yang digunakan untuk memvisualisasikan nilai tertentu yang diletakkan pada Form.
Graphics Menyediakan kemampuan menggambar pada sebuah Canvas.
Image Digunakan untuk menyimpan data gambar.
ImageItem Meyediakan kotrol layout untuk gambar-gambar yang ditempatkan pada sebuah Form.
Item Kelas dasar untuk menempatkan komponen-komponen yangdapat ditempatkan pada sebuah Form.
List Layar yang berisi daftar pilihan. Screen Kelas dasar semua komponen layar dalam high-level user interface.
StringItem Item yang berisi string yang kemudian ditempatkan pada Form.
TextBox Layar yang mengijinkan user memanipulasi teks dan bisa juga dijadikan media input.
TextField Komponen untuk memasukkan teks di atas Form. Ticker Bagian teks yang berjalan terus-menerus di atas layar.
Ticker tidak dapat ditempelkan pada Canvas.
. Read more "user interface..."
Labels:
java
MIDLET
Aplikasi J2ME
Mungkin sebagain kita telah mengenal Applet sebagai aplikasi Java yang berjalan pada internet yang bersifat client side atau Servlet yang bersifat server side. Sedangkan untuk aplikasi pada paket J2ME diberi nama Midlet.
Perangkat untuk Midlet
Untuk penjalankan Midlet tentunya diperlukan perangkat keras (device) yang mendukung Java, artinya perangkat tersebut harus memiliki Java Virtual Machine untuk menjalankan Midlet. Sekarang tidak susah lagi untuk menemui perangkat yang bisa menjalankan Midlet terutama untuk jenis ponsel. Hampir setiap ponsel keluaran terbaru telah menyertakan dukungan akan java MIDP.
Emulator Ponsel Java
Untuk menjalankan Midlet, programmer tidak perlu memiliki dan mencobanya pada ponsel. Cukup dengan emulator dari ponsel yang dapat dijalan pada PC.
Memulai program hello word
HelloWorld.java
import javax.microedition.midlet.*;
import javax.microedition.lcdui.*;
public class HelloWorld extends MIDlet {
private Display display;
private TextBox mainScreen;
public HelloWorld(){ display = Display.getDisplay(this);
mainScreen = new TextBox("Hello", "Hello Wolrd", 512, 1);
}public void startApp() { display.setCurrent(mainScreen);
}public void pauseApp() {
}public void destroyApp(boolean unconditional) {
}}
Ketika program diatas dijalankan menampilkan output berupa tulisan “Heloo World”. dan Untuk menutup aplikasi kita harus lewat tombol close di window layar emulator.
Read more "MIDLET..."
Mungkin sebagain kita telah mengenal Applet sebagai aplikasi Java yang berjalan pada internet yang bersifat client side atau Servlet yang bersifat server side. Sedangkan untuk aplikasi pada paket J2ME diberi nama Midlet.
Perangkat untuk Midlet
Untuk penjalankan Midlet tentunya diperlukan perangkat keras (device) yang mendukung Java, artinya perangkat tersebut harus memiliki Java Virtual Machine untuk menjalankan Midlet. Sekarang tidak susah lagi untuk menemui perangkat yang bisa menjalankan Midlet terutama untuk jenis ponsel. Hampir setiap ponsel keluaran terbaru telah menyertakan dukungan akan java MIDP.
Emulator Ponsel Java
Untuk menjalankan Midlet, programmer tidak perlu memiliki dan mencobanya pada ponsel. Cukup dengan emulator dari ponsel yang dapat dijalan pada PC.
Memulai program hello word
HelloWorld.java
import javax.microedition.midlet.*;
import javax.microedition.lcdui.*;
public class HelloWorld extends MIDlet {
private Display display;
private TextBox mainScreen;
public HelloWorld(){ display = Display.getDisplay(this);
mainScreen = new TextBox("Hello", "Hello Wolrd", 512, 1);
}public void startApp() { display.setCurrent(mainScreen);
}public void pauseApp() {
}public void destroyApp(boolean unconditional) {
}}
Ketika program diatas dijalankan menampilkan output berupa tulisan “Heloo World”. dan Untuk menutup aplikasi kita harus lewat tombol close di window layar emulator.
Read more "MIDLET..."
Labels:
java
java
Pembagian Paket Java
Java adalah teknologi dan bahasa pemrograman yang berjalan pada multiflatform sesuai dengan semboyannya yaitu “Write Once, Run Anywhere”.
Pada site official Java dari Sun yaitu
http://java.sun.com
bisa ditemui tiga pembagian paket Java yaitu :
Java 2 Enterprise Edition (J2EE).
Java 2 Standart Editon (J2SE).
Java 2 Micro Edition (J2ME).
Penjelasan paling simple atas pembagian tersebut adalah berdasarkan atas perangkat keras yang digunakan.
Paket J2EE digunakan pada perangkat keras yang mempunyai spesifikasi dan memory yang besar seperti pada komputer server.
Paket J2SE digunakan pada perangkat keras seperti komputer desktop.
Paket J2ME digunakan pada perangkat yang memiliki memory kecil seperti ponsel,pager atau PDA. Read more "java..."
Java adalah teknologi dan bahasa pemrograman yang berjalan pada multiflatform sesuai dengan semboyannya yaitu “Write Once, Run Anywhere”.
Pada site official Java dari Sun yaitu
http://java.sun.com
bisa ditemui tiga pembagian paket Java yaitu :
Java 2 Enterprise Edition (J2EE).
Java 2 Standart Editon (J2SE).
Java 2 Micro Edition (J2ME).
Penjelasan paling simple atas pembagian tersebut adalah berdasarkan atas perangkat keras yang digunakan.
Paket J2EE digunakan pada perangkat keras yang mempunyai spesifikasi dan memory yang besar seperti pada komputer server.
Paket J2SE digunakan pada perangkat keras seperti komputer desktop.
Paket J2ME digunakan pada perangkat yang memiliki memory kecil seperti ponsel,pager atau PDA. Read more "java..."
Labels:
java
YOGYAKARTA
Yogyakarta is one of the supreme cultural centers of Java. Full Gamelan orchestras visions from the past, classical and contemporary Javanese dances exhibit beautiful control and poise, wayang kulit-leather puppet theaters come to life and hundreds of other traditional illustrations of art keep locals and visitors spellbound. It is as if the city itself has an extraordinary life force and charms, which seldom fails to captivate. The province of Yogyakarta with its status as a special region lies in the Southern part of Central Java, in the heartland of Javanese culture. As the former capital and the center of several kingdoms in the past, this region and its people are very rich in a variety of cultures. It is widely known from to historical records that the civilization, art and culture had developed well in the center of those kingdoms respectively in the era of the Ancient Mataram Kingdom (8th - 10th Century) the second Mataram Kingdom (17th - 18th Century) and Sultanate Ngayogyokarto from the mid of 18th Century up today.
Yogyakarta is one of the supreme cultural centers of Java. Full Gamelan orchestras visions from the past, classical and contemporary Javanese dances exhibit beautiful control and poise, wayang kulit-leather puppet theaters come to life and hundreds of other traditional illustrations of art keep locals and visitors spellbound. It is as if the city itself has an extraordinary life force and charms, which seldom fails to captivate. The province of Yogyakarta with its status as a special region lies in the Southern part of Central Java, in the heartland of Javanese culture. As the former capital and the center of several kingdoms in the past, this region and its people are very rich in a variety of cultures. It is widely known from to historical records that the civilization, art and culture had developed well in the center of those kingdoms respectively in the era of the Ancient Mataram Kingdom (8th - 10th Century) the second Mataram Kingdom (17th - 18th Century) and Sultanate Ngayogyokarto from the mid of 18th Century up today. Read more "YOGYAKARTA..."
Yogyakarta is one of the supreme cultural centers of Java. Full Gamelan orchestras visions from the past, classical and contemporary Javanese dances exhibit beautiful control and poise, wayang kulit-leather puppet theaters come to life and hundreds of other traditional illustrations of art keep locals and visitors spellbound. It is as if the city itself has an extraordinary life force and charms, which seldom fails to captivate. The province of Yogyakarta with its status as a special region lies in the Southern part of Central Java, in the heartland of Javanese culture. As the former capital and the center of several kingdoms in the past, this region and its people are very rich in a variety of cultures. It is widely known from to historical records that the civilization, art and culture had developed well in the center of those kingdoms respectively in the era of the Ancient Mataram Kingdom (8th - 10th Century) the second Mataram Kingdom (17th - 18th Century) and Sultanate Ngayogyokarto from the mid of 18th Century up today. Read more "YOGYAKARTA..."
Labels:
wisata
BALI
Bali, a tropical island in the Indonesian archipelago, is an ideal holiday destination for all ages. It has a wonderful blend of modern tourist facilities combined with excellent shopping opportunities and a rich heritage. A unique aspect of Bali is its active Hindu culture. Many Hindu-Balinese rituals are reflected in daily life and can be seen in numerous ceremonies, Balinese festivals and magnificent temples and palaces. If you are a surfing enthusiast, Bali is definitely the place for you as some of the best surfing beaches in the world can be found on the western side of the island. Conversely the eastern side is a wonderful haven for families, with beautiful white sand beaches and gentle seas with little more than a ripple breaking the calm surface of the water.
A shopper's paradise, Bali is well known for casual and tailored clothing, locally-made jewellery, handicrafts, antiques and artefacts. Leather ware is one of the unexpected local bargains with everything from handbags to tailor-made leather jackets, all at unbelievable prices.
For those who enjoy water-related activities, Bali has world-class scuba diving and snorkelling day trips to fantastic sites. Enjoy a romantic moonlit dinner and watch a spectacular Balinese Fire Dance or Kecak Dance. If you want to dance the night away Bali certainly knows how to party and nightclubs are scattered everywhere. For those more culturally inclined, Bali can offer the peace and tranquillity of Ubud high in the hills where the scenery is nothing less than spectacular. In Ubud, one can discover all sorts of cultural treasures in this art capital of Bali and perhaps of all Indonesia. Jungle, picturesque hillsides, rice terraces and the magnificence of Kintamani Volcano are also waiting to be discovered. Bali is a truly international destination, offering every standard of accommodation ranging from modest bungalow style hotels in lush gardens or bustling towns, to exclusive, sophisticated hotels in either the jungles or along open stretches of beach or hidden in small bays.
Bali has a tropical climate all year. The average temperature hovers around 30 degrees Celsius year-round. There are dry and rainy seasons - dry from April to September and rainy from October to March. Read more "BALI..."
A shopper's paradise, Bali is well known for casual and tailored clothing, locally-made jewellery, handicrafts, antiques and artefacts. Leather ware is one of the unexpected local bargains with everything from handbags to tailor-made leather jackets, all at unbelievable prices.
For those who enjoy water-related activities, Bali has world-class scuba diving and snorkelling day trips to fantastic sites. Enjoy a romantic moonlit dinner and watch a spectacular Balinese Fire Dance or Kecak Dance. If you want to dance the night away Bali certainly knows how to party and nightclubs are scattered everywhere. For those more culturally inclined, Bali can offer the peace and tranquillity of Ubud high in the hills where the scenery is nothing less than spectacular. In Ubud, one can discover all sorts of cultural treasures in this art capital of Bali and perhaps of all Indonesia. Jungle, picturesque hillsides, rice terraces and the magnificence of Kintamani Volcano are also waiting to be discovered. Bali is a truly international destination, offering every standard of accommodation ranging from modest bungalow style hotels in lush gardens or bustling towns, to exclusive, sophisticated hotels in either the jungles or along open stretches of beach or hidden in small bays.
Bali has a tropical climate all year. The average temperature hovers around 30 degrees Celsius year-round. There are dry and rainy seasons - dry from April to September and rainy from October to March. Read more "BALI..."
Labels:
wisata
ICMP & TCP/IP
internet Control Message Protocol (ICMP) adalah
salah satu protokol inti dari keluarga protokol internet.
ICMP utamanya digunakan oleh sistem operasi komputer jaringan untuk mengirim pesan kesalahan yang menyatakan,
sebagai contoh, bahwa komputer tujuan tidak bisa dijangkau.
TCP/IP adalah salah satu jenis protokol (aturan) yg memungkinkan kumpulan komputer
dapat berkomunikasi dan bertukar data di dalam suatu network (jaringan).
Read more "ICMP & TCP/IP..."
salah satu protokol inti dari keluarga protokol internet.
ICMP utamanya digunakan oleh sistem operasi komputer jaringan untuk mengirim pesan kesalahan yang menyatakan,
sebagai contoh, bahwa komputer tujuan tidak bisa dijangkau.
TCP/IP adalah salah satu jenis protokol (aturan) yg memungkinkan kumpulan komputer
dapat berkomunikasi dan bertukar data di dalam suatu network (jaringan).
Read more "ICMP & TCP/IP..."
Labels:
network
sukses percaya diri
didalam hidup ini, kita di hadapkan dalam banyak hal, banyak kegiatan, banyak aturan, yang menbuat diri kita harus selalu tampil dengan percaya diri. akan tetapi masalahnya untuk mendapatkan kepercayaan diri di butuhkan banyak hal yang saling terkait di dalam diri kita, banyak orang yang gagal karena mereka tidak percaya diri, tidak pede di dalam mengambil sikap.para pembaca yang terhormat disini akan saya ungkap dan saya ajarkan tentang menjadi manusia yang mempunyai rasa kepercayan diri yang tangguh sebagai pengantar kesuksesan saudara. salah satu cara agar kita selalu tampil percaya diri adalah dengan melatih diri kita dari dalam, artinya adalah harus di awali dari diri kita sendiri, ada satu kisah yaitu pengalaman saya sendiri , pada waktu itu saya di suruh membawakan sebuah acara suatu organisasi di tempat saya, di situ saya di tuntut untuk berbicara di depan orang- orang yang sangat banyak sekali, tetapi karena saya kurangnya persiapan , dan di tambah lagi dengan penguasaan teori belum mendalam membuat saya kelabakan dan demam panggung sehingga membuat acara yang saya bawakan tidak sempurna hasil akhirnya,
ada beberapa tips agar kita bisa percaya diri
1. melatih diri kita setiap hari untuk tampil pede
2. kita harus menguasai rasa takut pada diri kita
3. kepribadian
melatih diri kita setiap hari untuk tampil pede
artinya dimana pun kita berada harus selalu tampil pede, di sekolah, di rumah, di kantor, di tempat-tempat umum, harus selalu kita tampil pede, dan jangan pernah malu untuk berkreasi, tunjukkan bahwa inilah aku, beginilah aku dengan kemampuanku, dan selalu tampil exsis di manapun kita berada
menguasai rasa takut pada diri kita
di manapun kita berada bila di hadapkan dengan banyak orang pasti muncul rasa takut pada diri kita, rasa deg-degan yang selalu membayangi setiap orang, akan tetapi rasa takut itu tidak akan hilang bila kita tidak hadapi, dan akan semakin bertambah sehingga membuat kita tidak percaya diri dan membuat diri kita hang ,seperti kebo dlongop, hehheheheh, blank, pikiran kita kosong tidak karuan jadinya.jadi yang paling penting adalah kita harus bisa menguasai rasa takut yang berada dalam diri kita.
kepribadian
disini salah satu kunci sukses seseoarang adalah percaya diri, di dalam percaya diri di butuhkan kepribadian yang baik, yang mantap, yang mempunyai pendirian yang kuat, yang menpunyai talenta yang mantap.untuk itu kita harus benar-benar menigkatklan potensi diri kita, meningkatkan keperibadian kita, karena dengan memdidik dam menggembleng kepribadian kita akan dengan sendirinya muncul kepercayan dalam diri kita.
dengan menguasai tiga tips dia atas saya yakin anda akan menjadi orang yang sukses, dan mempunyai masa depan yang cerah, dan anda akan menjadi orang yang tidak sia-sia dimata umum, damn selalu mempunyai pandangan hidup untuk maju ke depan, selalu tersenyum di manapun anda berada untuk menyambut dunia. Read more "sukses percaya diri..."
ada beberapa tips agar kita bisa percaya diri
1. melatih diri kita setiap hari untuk tampil pede
2. kita harus menguasai rasa takut pada diri kita
3. kepribadian
melatih diri kita setiap hari untuk tampil pede
artinya dimana pun kita berada harus selalu tampil pede, di sekolah, di rumah, di kantor, di tempat-tempat umum, harus selalu kita tampil pede, dan jangan pernah malu untuk berkreasi, tunjukkan bahwa inilah aku, beginilah aku dengan kemampuanku, dan selalu tampil exsis di manapun kita berada
menguasai rasa takut pada diri kita
di manapun kita berada bila di hadapkan dengan banyak orang pasti muncul rasa takut pada diri kita, rasa deg-degan yang selalu membayangi setiap orang, akan tetapi rasa takut itu tidak akan hilang bila kita tidak hadapi, dan akan semakin bertambah sehingga membuat kita tidak percaya diri dan membuat diri kita hang ,seperti kebo dlongop, hehheheheh, blank, pikiran kita kosong tidak karuan jadinya.jadi yang paling penting adalah kita harus bisa menguasai rasa takut yang berada dalam diri kita.
kepribadian
disini salah satu kunci sukses seseoarang adalah percaya diri, di dalam percaya diri di butuhkan kepribadian yang baik, yang mantap, yang mempunyai pendirian yang kuat, yang menpunyai talenta yang mantap.untuk itu kita harus benar-benar menigkatklan potensi diri kita, meningkatkan keperibadian kita, karena dengan memdidik dam menggembleng kepribadian kita akan dengan sendirinya muncul kepercayan dalam diri kita.
dengan menguasai tiga tips dia atas saya yakin anda akan menjadi orang yang sukses, dan mempunyai masa depan yang cerah, dan anda akan menjadi orang yang tidak sia-sia dimata umum, damn selalu mempunyai pandangan hidup untuk maju ke depan, selalu tersenyum di manapun anda berada untuk menyambut dunia. Read more "sukses percaya diri..."
Labels:
enterprenuership
Feb 17, 2010
Cek IP Address
IP Address is a unique identity for each computer connected to the network, both local and internet.
When you connect to the internet then the ISP (Internet Service Provider) you use will give you the IP address (public ip) automatically (IP address is different from the IP address for your local jaringn).
To check the IP address provided by your ISP when you connect to the internet, you can visit the site:
http://ip-adress.com
When you open the site it will automatically be displayed ip address, country, city and name of ISP ISP you use, for example as shown below:
Read more "Cek IP Address..."
When you connect to the internet then the ISP (Internet Service Provider) you use will give you the IP address (public ip) automatically (IP address is different from the IP address for your local jaringn).
To check the IP address provided by your ISP when you connect to the internet, you can visit the site:
http://ip-adress.com
When you open the site it will automatically be displayed ip address, country, city and name of ISP ISP you use, for example as shown below:
Read more "Cek IP Address..."
Labels:
network
create a password difficult burglarized
The way a hacker to guess our password among other things:
1. Brute-force attack, ie by trying all combinations, ranging from aaaa to zzzz, until a few characters. 2. Dictionary attack, ie by guessing using words in a dictionary, and combined with numbers or characters. 3. Personal information attack, by entering personal data such as phone numbers, date of birth, name of
boyfriend, zip code, and so on. A very weak password would be very easily broken into by hackers this
way. Example of a very weak password such as: • 123456, qwerty, asdf, this is because it is easy once people are typing on the keyboard combination. • password, mypassword, and others who use words in a dictionary (all languages). • date of birth, name of boyfriend, and the other is the data that person.
Weak passwords can be broken in a faster time, for example: • using all lowercase. • use a combination of words and numbers, for example buku10, teroris80. • replacing letters with characters, such as c1nt @
How strong password and difficult to penetrate a hacker?
1. Is a combination of uppercase, lowercase, numbers, and characters. 2. The length of more than 10 characters. 3. Does not include the words in the dictionary. Strong passwords should be easily remembered by the owner. Examples of strong passwords: 1mAu $ 100Ribu How to remember: • 1 = the word "I" translated in English (I). • wanted = want • $ = cash • 100Ribu = 100 thousand Examples of strong passwords are: yellow-> 0 +1 Gul How to remember: • yellow = instance name for your sepesial: Naning • -> = arrows is identical to • 0 + = symbol girl • 1 = means the number one or at most • Gul = sugar is sweet
Some tips:1. Do not use the same password for various services, such as your email password as the password
friendster. This means: o someone who can break your myspace password, can also break down your email password.
While in the eyes of myspace password hacker to break more easily than a Yahoo email break. o admin or "people in" friendster know your password, he may also enter their password to your
email.2. Do not click the link in the email stating you must verify your password. This message was sent by hackers.3. Do not enter a password in addition to our site that provide services. For example do not enter a
password in yahoo friendster site for any reason (such as import address book).4. Before you log into an email or something else, make sure the URL in your browser correctly. For example
mail.yahoo.com not mail.yahoo-yahoo-ltd.com or verify.com or another.5. For online accounts such as e-gold, click the BCA, paypal, you should not type your password via the
keyboard (because hackers can read your keyboard keylogger program). Use the On Screen Keyboard,
Charakter Map, or copy and paste the random letters.
Okey so these tips to our password hacker difficult burglarized. Hopefully with these tips on our account
secure and protected from penetration.
copyright from http://tutorialgratis.wordpress.com Read more "create a password difficult burglarized..."
1. Brute-force attack, ie by trying all combinations, ranging from aaaa to zzzz, until a few characters. 2. Dictionary attack, ie by guessing using words in a dictionary, and combined with numbers or characters. 3. Personal information attack, by entering personal data such as phone numbers, date of birth, name of
boyfriend, zip code, and so on. A very weak password would be very easily broken into by hackers this
way. Example of a very weak password such as: • 123456, qwerty, asdf, this is because it is easy once people are typing on the keyboard combination. • password, mypassword, and others who use words in a dictionary (all languages). • date of birth, name of boyfriend, and the other is the data that person.
Weak passwords can be broken in a faster time, for example: • using all lowercase. • use a combination of words and numbers, for example buku10, teroris80. • replacing letters with characters, such as c1nt @
How strong password and difficult to penetrate a hacker?
1. Is a combination of uppercase, lowercase, numbers, and characters. 2. The length of more than 10 characters. 3. Does not include the words in the dictionary. Strong passwords should be easily remembered by the owner. Examples of strong passwords: 1mAu $ 100Ribu How to remember: • 1 = the word "I" translated in English (I). • wanted = want • $ = cash • 100Ribu = 100 thousand Examples of strong passwords are: yellow-> 0 +1 Gul How to remember: • yellow = instance name for your sepesial: Naning • -> = arrows is identical to • 0 + = symbol girl • 1 = means the number one or at most • Gul = sugar is sweet
Some tips:1. Do not use the same password for various services, such as your email password as the password
friendster. This means: o someone who can break your myspace password, can also break down your email password.
While in the eyes of myspace password hacker to break more easily than a Yahoo email break. o admin or "people in" friendster know your password, he may also enter their password to your
email.2. Do not click the link in the email stating you must verify your password. This message was sent by hackers.3. Do not enter a password in addition to our site that provide services. For example do not enter a
password in yahoo friendster site for any reason (such as import address book).4. Before you log into an email or something else, make sure the URL in your browser correctly. For example
mail.yahoo.com not mail.yahoo-yahoo-ltd.com or verify.com or another.5. For online accounts such as e-gold, click the BCA, paypal, you should not type your password via the
keyboard (because hackers can read your keyboard keylogger program). Use the On Screen Keyboard,
Charakter Map, or copy and paste the random letters.
Okey so these tips to our password hacker difficult burglarized. Hopefully with these tips on our account
secure and protected from penetration.
copyright from http://tutorialgratis.wordpress.com Read more "create a password difficult burglarized..."
Labels:
network
Jan 28, 2010
convert FAT to NTFS
convert FAT ke NTFS
step 1
into comandline type cd\
step2
into commandline type help convert
step3
suppose we want to change the D drive partition is a FAT file extension to NTFS.
into commandline type convert D: /FS:NTFS Read more "convert FAT to NTFS..."
step 1
into comandline type cd\
step2
into commandline type help convert
step3
suppose we want to change the D drive partition is a FAT file extension to NTFS.
into commandline type convert D: /FS:NTFS Read more "convert FAT to NTFS..."
Labels:
tips
solar powered lamp
This is a pretty good light is available in different colors, this beda.lampu was using solar power.
This light color options there are 3 kinds;
1.pink
2.yellow
3.blue
This form and color options available
how to charge the lamp is quite simple, do not need to be placed directly under the hot sun, just placed near the glass window in the sun.
The following is a specification of the lamp
for friends who are interested and want to buy it, these lights are sold around £ 20.00. please kalu wants to buy can buy here Read more "solar powered lamp..."
This light color options there are 3 kinds;
1.pink
2.yellow
3.blue
This form and color options available
how to charge the lamp is quite simple, do not need to be placed directly under the hot sun, just placed near the glass window in the sun.
The following is a specification of the lamp
for friends who are interested and want to buy it, these lights are sold around £ 20.00. please kalu wants to buy can buy here Read more "solar powered lamp..."
Labels:
tecnologi
Jan 27, 2010
strongest mobile
Land Rover car company to introduce Mobile with a Land Rover S1, Mobile was created as an alias Mobile strongest in the world is not damaged.
This new mobile phone made by Land Rover, known as the most powerful phone in the world.
This phone can still be used even though trampled by the elephant, heated with an oven, drowned dilumpur, and resistant to water with a depth of 1 meter.
This phone brings the 1500-hour battery life, 2.0 megapixel camera and extra loud ringtone to be heard in noisy environments because of the engine.
this phone marketed by Tesco with the price of £ 249.99 Pounds Sterling. Tesco believes that this phone will not be damaged, Tesco 3-year warranty. Read more "strongest mobile..."
Labels:
gadget
Jan 23, 2010
k-ninja
ini ada aplikasi yang menurutku sangat bagus dan wajib digunakan bagi temen2x yang mengutamakan kecepatan dalam browser.nama aplikasi web browser ini adalah K-NINJA.
K. Ninja adalah salah satu tool browser. Setelah melihat - melihat features dari browser ini saya jadi tertarik dan yakin kalo browser ini handal dan bisa membuat kita browsing internet lebih cepat dan mampu menambah kecepatan koneksi internet kita ketika sedang browsing.
dibawah ini adlah tampilan utama dari K-NINJA.
jika dilihat memeang tampilan aplikasi ini tidak seperti web browser,tapi jangan salah meskipun terlihat sederhana,kemampuan aplikasi ini melebihi web browser lainnya.hal ini terbukti dari fitur-fitur yang ada.
Dengan interface yang benar2 friendly dan tidak bnyak menggunakan RAM / memory pc kita menjadikan Tool Browser ini benar-benar ringan dan cepat untuk digunakan, berikut ini adalah beberapa fitur K. Ninja
K-Ninja Samurai Features:
- Rendering Engine - K-Ninja utilizes the latest SeaMonkey/Gecko Rendering Engine release: v1.8.1.2. It is a fast, secure rendering engine which supports most current Web Standards (HTML 4.0, CSS, XHTML etc.).
- Tabs - K-Ninja has tabbed browsing, which we call “Layers”. New layers can be opened and closed with the Open & Close Layers buttons.
- Compact Menu - to increase viewing space, the menu which is normally located at the top of the screen is available in K-Ninja via the Preferences button, by right-clicking on it.
- Pop-up Blocker - Enabled by default, K-Ninja will block most if not all pop-ups. The pop-up blocker can be enabled/disabled via the Preferences button.
- Integrated Search - just type a search term/word into the address bar, and click on the Search button. Results are then delivered via Google.
- RSS Support - the Aggreg8 RSS Reader is included with K-Ninja. It can be accessed via the Compact Menu (right-click on the Preferences button).
- Mouse Gestures - the mouse gestures plugin is included. To use simply right-click, hold the mouse button and then drag the cursor either right (to go back a page) or left (to go forward).
- Translate a Page - simply right-clicking on a webpage will provide you with a menu to translate a page from one language to another.
- Safe Recovery - Requires manually selecting the Open Last Session Feature.
- Unique Speed Settings - K-Ninja is by default optimized for fast connections, and these speed settings can now be toggled in case you are on dial-up.
- Mozilla ActiveX Control support included for Media Player functionality on streaming and embedded multimedia content.
- Flashblock extension - this can be enabled/disabled via the Compact Menu. Once enabled Flash animations will be deactivated on the webpages you are viewing.
- Quicknote extension - this is a handy little note-taking utility included in K-Ninja for those who like to take/transcribe notes or copy & paste text whilst browsing.
- Extremely lightweight STP MP3 Player included (200kb). When run an icon for STP will appear in your System Tray. Right click on the icon for options or to play an MP3 or CD whilst browsing.
- Includes additional Web Search engines including MultiSearch: enter a search term and the results will be delivered via 6 popular search engines including Google (100 results per page), MSN, All The Web, Google Images, Ask.com & Gigablast.
- URL Shortcut Hotkeys now implemented.
- Built in macro language.
- Unique themes & skins.
- Even more privacy options available via the Compact Menu. It will provide you with an array of options to enable/disable any “features” that you don´t want running on a webpage before you view it (like Java, Javascript etc).
download Read more "k-ninja..."
Labels:
aplication
facebook+YM
This is a pretty good application for mengabungkan various social networking and instant message sperti facebook, twitter, yahoo messenger, AIM, and several other instant messege. In other words, you can follow the status updates from your friends on facebook, twitter, etc. from Yono Desktop ini.tampilan this application is quite trendy and attractive.

To use this free software is very easy way. After you finish installing the account you just add whatever you want to enable the Yoono Desktop.
such an account you want to enable your facebook, you can click on an account that is facebook, it would appear the display;

Here you need to fill in your email and password. After you click the Login button will display a confirmation page for Facebook to connect with Yoono Desktop. Klik aja Allow button.
an account to add other similar way.
download yono desktop in here Read more "facebook+YM..."

To use this free software is very easy way. After you finish installing the account you just add whatever you want to enable the Yoono Desktop.
such an account you want to enable your facebook, you can click on an account that is facebook, it would appear the display;

Here you need to fill in your email and password. After you click the Login button will display a confirmation page for Facebook to connect with Yoono Desktop. Klik aja Allow button.
an account to add other similar way.
download yono desktop in here Read more "facebook+YM..."
Labels:
aplication
yono desktop
ini ada aplikasi yang cukup bagus buat mengabungkan berbagai sosial networking dan instant message sperti facebook, twitter, yahoo messenger,AIM, dan beberapa instant messege lainnya. Dengan kata lain Anda dapat mengikuti update status dari teman-teman Anda di facebook, twitter, dll tersebut dari Yono Desktop ini.tampilan aplikasi ini cukup trendy dan juga menarik.
berikut screenshoot dari aplikasi yono desktop;
Untuk menggunakan software gratis ini caranya sangat mudah. Setelah Anda selesai menginstall maka Anda tinggal menambahkan akun apa saja yang ingin Anda aktifkan di Yoono Desktop ini.
misalnya anda ingin mengaktifkan acount facebook anda, anda tinggal klik acount facebook yang ada, maka akan muncul tampilan;
Di sini Anda harus mengisikan email dan password Anda. Setelah Anda mengklik tombol Login maka akan muncul halaman konfirmasi untuk menghubungkan Facebook dengan Yoono Desktop. Klik aja tombol Allow.
untuk menambahkan acount yang lainnya caranya sama.
untuk download yono desktop di sini Read more "yono desktop..."
berikut screenshoot dari aplikasi yono desktop;
Untuk menggunakan software gratis ini caranya sangat mudah. Setelah Anda selesai menginstall maka Anda tinggal menambahkan akun apa saja yang ingin Anda aktifkan di Yoono Desktop ini.
misalnya anda ingin mengaktifkan acount facebook anda, anda tinggal klik acount facebook yang ada, maka akan muncul tampilan;
Di sini Anda harus mengisikan email dan password Anda. Setelah Anda mengklik tombol Login maka akan muncul halaman konfirmasi untuk menghubungkan Facebook dengan Yoono Desktop. Klik aja tombol Allow.
untuk menambahkan acount yang lainnya caranya sama.
untuk download yono desktop di sini Read more "yono desktop..."
Labels:
aplication
merubah text menjadi kode ASCII
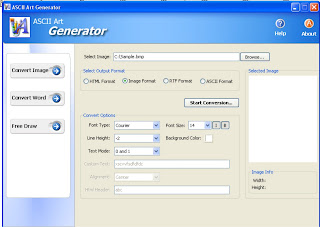
setelah beberapa lama gak update blog,sekarang saatnya aku post sedikit artikel.
bagi temen2x yang yang ingin membuat karya seni dengan mengunakan kode ASCII sekarang tidak perlu lagi binggung bangaimana membuatnya, cukup melakukan beberapa langkah saja karya seni temen2x sudah jadi.
caranya unduh program ASCII art generator (bisa di searching dari google) dan instal program tersebut pada komputer/laptop temen2x.jalan kan aplikasi tersebut.
berikut tampilan awal dari program tersebut:
program ini terdiri dari 3 menu utama,yaitu;
1.convert image
2.convert word
3.free draw
jika temen2x ingin membuat kata dengan karakter ASCII berikut caranya;
1.klik pada menu convert word
2.ketikkan kata yang ingin diubah kedalam karakter ASCII pada kolom
char config word(s)atur ukuran font dan type sesuai keinginan kamu.
3.setelah itu klik start convertion,maka kata tersebut akan di ubah kedalam karakter
ASCII.
4.setelah itu tinggal save as/copy ketempat yang temen2x kehendaki.
NB; cara untuk mengunakan menu lainnya hampir sama.
Read more "merubah text menjadi kode ASCII..."
bagi temen2x yang yang ingin membuat karya seni dengan mengunakan kode ASCII sekarang tidak perlu lagi binggung bangaimana membuatnya, cukup melakukan beberapa langkah saja karya seni temen2x sudah jadi.
caranya unduh program ASCII art generator (bisa di searching dari google) dan instal program tersebut pada komputer/laptop temen2x.jalan kan aplikasi tersebut.
berikut tampilan awal dari program tersebut:
program ini terdiri dari 3 menu utama,yaitu;
1.convert image
2.convert word
3.free draw
jika temen2x ingin membuat kata dengan karakter ASCII berikut caranya;
1.klik pada menu convert word
2.ketikkan kata yang ingin diubah kedalam karakter ASCII pada kolom
char config word(s)atur ukuran font dan type sesuai keinginan kamu.
3.setelah itu klik start convertion,maka kata tersebut akan di ubah kedalam karakter
ASCII.
4.setelah itu tinggal save as/copy ketempat yang temen2x kehendaki.
NB; cara untuk mengunakan menu lainnya hampir sama.
Labels:
aplication
Jan 2, 2010
overclock
Language Overclock composed of two words that is Over and that means Clock mainboard setup for the processor clock and a VGA, and can also maximize the performance of certain software does is run the computer at a higher clock speed than the specifications, Wikipedia says, Overclock it means to run a component above the computer clock rate than it should.
WHAT PURPOSE OF overclock BY YOU?
CPU Bus Clock and Clock on this overclock, it is important to know the concept of the CPU clock and bus clock. CPU clock is a clock signal in the CPU, including the processor. CPU clock is what is often called the processor specification. Example Pentium 4 2.4 GHz. This means that these processors have allocated 2.4 GHz CPU clock. Clock does not watch or clock. Here is a signal that is used by the processor to trigger the occurrence of a process.
Read more "overclock..."
WHAT PURPOSE OF overclock BY YOU?
CPU Bus Clock and Clock on this overclock, it is important to know the concept of the CPU clock and bus clock. CPU clock is a clock signal in the CPU, including the processor. CPU clock is what is often called the processor specification. Example Pentium 4 2.4 GHz. This means that these processors have allocated 2.4 GHz CPU clock. Clock does not watch or clock. Here is a signal that is used by the processor to trigger the occurrence of a process.
Read more "overclock..."
Labels:
pc
artificial intelligence
1. Processing (pefokusan) filed / ditunjkkan on issues that do not respond to a problem.
2. More effort is intended to capture and manipulate nature - an important qualitative properties of a situation
3. Work done adalahuntuk handling and simantik and syntactic forms
4. Answer yangdiberikan not optimal but rather
5. The use of special besarpengetahuan issues dalammemecahkakn
6. The use of meta-level pengeraitahuan to influence the control strategy
a problem
Read more "artificial intelligence..."
2. More effort is intended to capture and manipulate nature - an important qualitative properties of a situation
3. Work done adalahuntuk handling and simantik and syntactic forms
4. Answer yangdiberikan not optimal but rather
5. The use of special besarpengetahuan issues dalammemecahkakn
6. The use of meta-level pengeraitahuan to influence the control strategy
a problem
Read more "artificial intelligence..."
Labels:
intelligence,
pc
hacker history
erminology hackers emerged in the early 1960s among the members of student organizations Tech Model Railroad Club in Artifisial Intelligence Laboratory Massachusetts Institute of Technology (MIT). Student group is one of the pioneers of computer technology and they struggled with a number of mainframe computers. Said the first time hackers came up with a positive sense to refer to a member who has expertise in the field of computers and able to make computer programs better than what has been designed together.
Then in 1983, the term hacker became negative. The problem, in that year for the first time the FBI arrested a criminal group of computers The 414s are based in Milwaukee USA. 414 is their local area code. The group that came to be called a hacker was convicted of burglary 60 computers, from computers owned by Cancer Center Memorial Sloan-Kettering's computer to Los Alamos National Laboratory. One of the perpetrators are getting immunity for TESTIMONIALS, while the other 5 players get probation sentence.
Then, further up other groups to mention themselves hackers, but it's not. They are (especially the men) who have the satisfaction of breaking through computer and phone-jockey (phreaking). True hackers call these people 'crackers' and do not like to hang out with them. True hackers crackers as people look lazy, irresponsible, and not too bright. Real hackers do not agree to say that with a person through the security has become a hacker.
The hackers meeting each year which is held once every mid-July in Las Vegas. A meeting of the world's largest hacker is called Def Con. Def Con event to event is more exchange of information and technology related to hacking activities.
Hacker has a negative connotation for the public misunderstanding of the difference terms of the hackers and crackers. Many people understand that the resulting losses hackerlah certain parties such as changing the look of a web site (Defacing), insert the virus code and so on. In fact, they are a cracker. Crackerlah using vulnerabilities that have not been repaired by the software maker (bug) to infiltrate and damage a system. For this reason, hackers often understood is divided into 2 groups White Hat Hackers, the true hackers and crackers are often referred to as Black Hat Hackers.
White hat is a term of information technology in the English language that refers to the ethical hackers showed a weakness in a computer system. White hat generally focuses its action on how to protect a system, which contradicts with the black hat is more focus on how the action through the system.
Black hat hacker is a term of information technology in English which refer to those hackers who break computer security without permission, usually in order to access computers that are connected to the network. The term cracker proposed by Richard Stallman to refer in this sense. Read more "hacker history..."
Then in 1983, the term hacker became negative. The problem, in that year for the first time the FBI arrested a criminal group of computers The 414s are based in Milwaukee USA. 414 is their local area code. The group that came to be called a hacker was convicted of burglary 60 computers, from computers owned by Cancer Center Memorial Sloan-Kettering's computer to Los Alamos National Laboratory. One of the perpetrators are getting immunity for TESTIMONIALS, while the other 5 players get probation sentence.
Then, further up other groups to mention themselves hackers, but it's not. They are (especially the men) who have the satisfaction of breaking through computer and phone-jockey (phreaking). True hackers call these people 'crackers' and do not like to hang out with them. True hackers crackers as people look lazy, irresponsible, and not too bright. Real hackers do not agree to say that with a person through the security has become a hacker.
The hackers meeting each year which is held once every mid-July in Las Vegas. A meeting of the world's largest hacker is called Def Con. Def Con event to event is more exchange of information and technology related to hacking activities.
Hacker has a negative connotation for the public misunderstanding of the difference terms of the hackers and crackers. Many people understand that the resulting losses hackerlah certain parties such as changing the look of a web site (Defacing), insert the virus code and so on. In fact, they are a cracker. Crackerlah using vulnerabilities that have not been repaired by the software maker (bug) to infiltrate and damage a system. For this reason, hackers often understood is divided into 2 groups White Hat Hackers, the true hackers and crackers are often referred to as Black Hat Hackers.
White hat is a term of information technology in the English language that refers to the ethical hackers showed a weakness in a computer system. White hat generally focuses its action on how to protect a system, which contradicts with the black hat is more focus on how the action through the system.
Black hat hacker is a term of information technology in English which refer to those hackers who break computer security without permission, usually in order to access computers that are connected to the network. The term cracker proposed by Richard Stallman to refer in this sense. Read more "hacker history..."
Labels:
hacker
manifesto hacker
It happened again today. Another one sold out, sacrificing their dreams to the corporate security machine.
Damn whitehats, noone believes in a cause anymore.
Another bug was released today to the security mailing lists.
Damn Whitehats, they know not what they do.
Another potential computer genius was relegated to an existence of nothing more than a 9-5 cubicle-dwelling promotional tool.
Damn whitehats, putting money before discovery.
Another family was ravaged by cooperations and governments bent on instituting control over individuality, monitoring every action..
Another kid was sentenced today for searching for a way to understand the world. Convicted and imprisoned, not because of what he did, but because of what others thought he could do.
Damn Whitehats - Fear keeps them in business.
The public, believing anything it hears from "reputed experts". Screaming for blood. Looking for something to blame for their lost hope. Their lost ability to seek out new knowledge. Fear consumes them. They cannot let go of their uncertainty and doubt because there is no meaning. They seek to destroy explorers, outlaws, curiosity seekers because they are told too. They are told these people that seek information are evil. Individuality is evil. Judgment should be made based upon a moral standard set in conformity rather than resistance. Lives are ruined in the name of corporate profit and information is hoarded as a commodity.
Damn Whitehats, you were once like us.
I was a Whitehat. I had an awakening. I saw the security industry for what is really is. I saw the corruption, the lies, the deceit, the extortion of protection money in the form of subscription services and snake-oil security consultants.
I wanted to know, I wanted to understand, I wanted to go further then the rest. I never want to be held down by contracts and agreements.
You say I should grow up. You say I should find better things to do with my time. You say I should put my talent to better use. You're saying I should fall in line with the other zombies and forget everything I believe in and shun those with my drive, my curiosity, tell them it's not worth it, deny them of the greatest journey they will ever experience in their lives.
I am not a blackhat. The term is insulting, it implies I am the opposite of you. You think i seek to defeat security, when I seek something greater. I will write exploits, travel through networks, explore where you are afraid to go. I will not put myself in the spotlight and release destructive tools to the public to attract business. I will not feed the fear and hysteria created by the security industry to increase stock prices. I can, and will, code and hack and find out everything I can for the same reasons I did years ago.
I am a Hacker, dont try to understand me, you lost all hope of that when you crossed the line. You fail to see the lies and utter simplicity behind the computer security industry. Once, you may have shared my ideals. You fail to see the fact that security is a maintenance job.
Youve given up hope for something better. You fail to see yourself as worthless, fueling an industry whose cumulative result is nothing. I dont hate you, I dont even really care about you - If you try to stop me, you will fail, because I do this out of love -- you do it for money.
This is our world now.. the world of the electron and the switch, the beauty of the baud. We make use of a service already existing without paying for what could be dirt cheap if it wasn't run by profiteering gluttons, and you call us criminals. We explore... and you call us criminals. We seek after knowledge... and you call us criminals. We exist without skin color, without nationality, without religious bias... and you call us criminals. You build atomic bombs, you wage wars, you murder, cheat and lie to us and try to make us belive it is for our own good, yet we're the ciminals.
Yes, I am a criminal. My crime is that of curiosity. My crime is that of judging people by what they say and think, not what they look like. My crime is that of outsmarting you, something that you will never forgive me for.
I am a Hacker, and this is my manifesto. You can't stop me, and you certainly can't stop us all.
Read more "manifesto hacker..."
Damn whitehats, noone believes in a cause anymore.
Another bug was released today to the security mailing lists.
Damn Whitehats, they know not what they do.
Another potential computer genius was relegated to an existence of nothing more than a 9-5 cubicle-dwelling promotional tool.
Damn whitehats, putting money before discovery.
Another family was ravaged by cooperations and governments bent on instituting control over individuality, monitoring every action..
Another kid was sentenced today for searching for a way to understand the world. Convicted and imprisoned, not because of what he did, but because of what others thought he could do.
Damn Whitehats - Fear keeps them in business.
The public, believing anything it hears from "reputed experts". Screaming for blood. Looking for something to blame for their lost hope. Their lost ability to seek out new knowledge. Fear consumes them. They cannot let go of their uncertainty and doubt because there is no meaning. They seek to destroy explorers, outlaws, curiosity seekers because they are told too. They are told these people that seek information are evil. Individuality is evil. Judgment should be made based upon a moral standard set in conformity rather than resistance. Lives are ruined in the name of corporate profit and information is hoarded as a commodity.
Damn Whitehats, you were once like us.
I was a Whitehat. I had an awakening. I saw the security industry for what is really is. I saw the corruption, the lies, the deceit, the extortion of protection money in the form of subscription services and snake-oil security consultants.
I wanted to know, I wanted to understand, I wanted to go further then the rest. I never want to be held down by contracts and agreements.
You say I should grow up. You say I should find better things to do with my time. You say I should put my talent to better use. You're saying I should fall in line with the other zombies and forget everything I believe in and shun those with my drive, my curiosity, tell them it's not worth it, deny them of the greatest journey they will ever experience in their lives.
I am not a blackhat. The term is insulting, it implies I am the opposite of you. You think i seek to defeat security, when I seek something greater. I will write exploits, travel through networks, explore where you are afraid to go. I will not put myself in the spotlight and release destructive tools to the public to attract business. I will not feed the fear and hysteria created by the security industry to increase stock prices. I can, and will, code and hack and find out everything I can for the same reasons I did years ago.
I am a Hacker, dont try to understand me, you lost all hope of that when you crossed the line. You fail to see the lies and utter simplicity behind the computer security industry. Once, you may have shared my ideals. You fail to see the fact that security is a maintenance job.
Youve given up hope for something better. You fail to see yourself as worthless, fueling an industry whose cumulative result is nothing. I dont hate you, I dont even really care about you - If you try to stop me, you will fail, because I do this out of love -- you do it for money.
This is our world now.. the world of the electron and the switch, the beauty of the baud. We make use of a service already existing without paying for what could be dirt cheap if it wasn't run by profiteering gluttons, and you call us criminals. We explore... and you call us criminals. We seek after knowledge... and you call us criminals. We exist without skin color, without nationality, without religious bias... and you call us criminals. You build atomic bombs, you wage wars, you murder, cheat and lie to us and try to make us belive it is for our own good, yet we're the ciminals.
Yes, I am a criminal. My crime is that of curiosity. My crime is that of judging people by what they say and think, not what they look like. My crime is that of outsmarting you, something that you will never forgive me for.
I am a Hacker, and this is my manifesto. You can't stop me, and you certainly can't stop us all.
Read more "manifesto hacker..."
Labels:
hacker
HACKER
1. Hacker Definition
Hackers are in Indonesian language is called hackers are people who study, analyze, and then if wanted, can create, modify, or even exploit the system contained in a device such as computer software and computer hardware such as computer programs, and administrative matters other, especially security. [Wikipedia, 2009]
From time to time the definition of "hacker" has evolved, but at this time can be defined as "people who enjoy learning the ins and outs of comp system. And experimenting with it. "Eric Raymond, author of" The New Hacker's Dictionary (MIT Press 1994), writing features hackers as follows:
- Joy of studying detail comp system. Or programming language.
- Joy to the practice of programming rather than just menteorikannya
- Respecting others hacing results.
- Learn programming with the rapid
- Advanced in the operating system / language specific programming (Unix)
True hackers are not criminal groups such as the belief network of destruction of many, but it must be admitted that from time to time there are quite a lot of abuse by hackers use their skills and to pengethuan things destructive and negative, do various crimes or doing meddling with the mess and damage files of [Artha, 2001]
Hacker is a set or some group that aims to develop science pengengetahuan and sharing information freely with no limits. Hacker is someone who is interested to know in depth about the work of a system, computer, or computer network. They consist of the network expert programmers. They, too, who contributed to build the Internet through the development of the UNIX operating system [Syrozone, 2009]
Hacking is a computer program through the activities of others to. Hacker is someone who likes to explore computers, have the expertise to make and read a particular program, and obsessed with watching the security (security) it. Hacker has a double face; there is something dear thief [Poskota, 2009] Read more "HACKER..."
Hackers are in Indonesian language is called hackers are people who study, analyze, and then if wanted, can create, modify, or even exploit the system contained in a device such as computer software and computer hardware such as computer programs, and administrative matters other, especially security. [Wikipedia, 2009]
From time to time the definition of "hacker" has evolved, but at this time can be defined as "people who enjoy learning the ins and outs of comp system. And experimenting with it. "Eric Raymond, author of" The New Hacker's Dictionary (MIT Press 1994), writing features hackers as follows:
- Joy of studying detail comp system. Or programming language.
- Joy to the practice of programming rather than just menteorikannya
- Respecting others hacing results.
- Learn programming with the rapid
- Advanced in the operating system / language specific programming (Unix)
True hackers are not criminal groups such as the belief network of destruction of many, but it must be admitted that from time to time there are quite a lot of abuse by hackers use their skills and to pengethuan things destructive and negative, do various crimes or doing meddling with the mess and damage files of [Artha, 2001]
Hacker is a set or some group that aims to develop science pengengetahuan and sharing information freely with no limits. Hacker is someone who is interested to know in depth about the work of a system, computer, or computer network. They consist of the network expert programmers. They, too, who contributed to build the Internet through the development of the UNIX operating system [Syrozone, 2009]
Hacking is a computer program through the activities of others to. Hacker is someone who likes to explore computers, have the expertise to make and read a particular program, and obsessed with watching the security (security) it. Hacker has a double face; there is something dear thief [Poskota, 2009] Read more "HACKER..."
Labels:
hacker
A. CRACKER
Cracker. Is the dark side of computer security professionals who stray too far. The script kiddies, the Black Hat, the people without knowledge except how to do hacking. This group does not know how the computer works. A cracker does not care about the community and not think about consequences of their actions. The Cracker despised in hacking forums and identical to the damage and "Google". The cracker want everything under their control are stored in the record. They do not seek information for themselves and depend on anyone who gave it to them. They were what people want to-be. [Teguhramadhan, 2004]
Cracker is a term for people looking for weaknesses to the system and enter personal interests and make a profit from the system in enter such as: the theft of data, deletion, and many others. The young cracker cracking is generally done to improve / use of network resources for its own sake.
Read more "A. CRACKER..."
Cracker is a term for people looking for weaknesses to the system and enter personal interests and make a profit from the system in enter such as: the theft of data, deletion, and many others. The young cracker cracking is generally done to improve / use of network resources for its own sake.
Read more "A. CRACKER..."
Labels:
hacker
Subscribe to:
Posts (Atom)